An incident is a breach of security. Actions taken to resolve and remediate the threat are known as Incident Response.
Incidents are classified using a rating of urgency and impact. Urgency is determined by the type of attack faced. Impact is determined by the affected system and what impact that has on business operations.
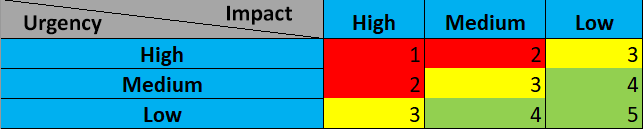
An incident is responded to by csirt).
Phases
There are 6 phases of IR:
- Preparation
- Do we have the resources and plans in place to deal with the security incident?
- Identification
- Has the threat and the threat actor been correctly identified in order for us to respond to?
- Containment
- Can the threat/security incident be contained to prevent other systems or users from being impacted?
- Eradication
- Remove the active threat.
- Recovery
- Perform a full review of the impacted systems to return to business as usual operations.
- Lessons Learned
- What can be learnt from the incident?